by Nicholas Martin – Fraunhofer Institute for Systems and Innovation Research ISI
Electronic Identity (eID) solutions in the public sector have often suffered from low adoption, in turn retarding the development of e-government. An important question is whether SSI-style eID solutions can help to break this cycle.
Electronic identity schemes are not a new invention. Indeed, as the previous post in this blog about electronic identities in Iceland illustrates, in many European countries schemes based on a variety of technical foundations already exist to some extent [1]. Nevertheless, self-sovereign identity (SSI) marks a genuinely novel approach to identity management. This raises the question of what the larger social, economic or political benefits and implications (if any) of SSI may be, especially for use in the public sector and e-government..
SSI and other electronic identity schemes
Several different approaches and, to some extent, generations of electronic identity (eID) schemes can be distinguished. As described in [2, 3] and the first post in this blog series:
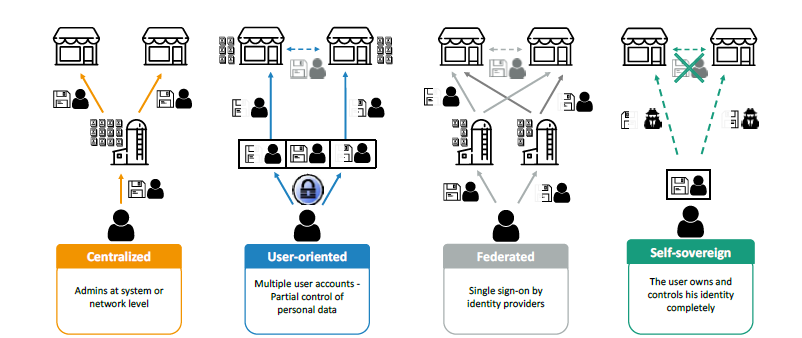
- In centralised or siloed identity management systems, a central entity (e.g., a social security bureau) manages the user’s identity, issuing her with an identifier, and storing and controlling access to her data, which is used exclusively for this service. The user has limited transparency into and control over how her data is used. These factors increase the risk of data misuse. At the same time, centralised systems are generally not interoperable: the user cannot use the identifier or the stored data for another service. Instead, she has to create or receive an identifier for each different service, resulting in redundant data holdings and numerous identifiers, increasing security vulnerabilities.
- In user-oriented systems, the user manages her identifiers and access to different services herself (e.g., by creating and maintaining usernames and passwords for diverse online services). However, the data associated with the identifier, and the identifier itself, are also known to the service providers, and can be passed between providers outside of the user’s knowledge or control. Again, multiple identifiers and passwords (or similar) create security vulnerabilities, and despite providers’ ability to share data among each other, there is no interoperability between the services’ identity management systems, so that the user must regularly provide the same data again and again.
- Federated or single sign-on identity approaches constitute a further development. Here, a central entity provides the user with an identifier (e.g., a social network, providing a username and password; or a state agency, providing a universal smartcard) that she can use to identify herself and share data across multiple service providers. The central entity functions as an intermediary between the user and the service provider(s). While the interoperability of federated identity systems is convenient – the user now only needs a single identifier and does not need to provide the same data over and over again – they threaten severe privacy loss and security vulnerabilities, as the central instance is able to track the user across the different services accessed.
- Self-sovereign identity (SSI) schemes, finally, seek to provide the user with full control over her identity (identifier, associated data, ability to prove the accuracy of these to service providers), by enabling her to store these securely on her smartphone (or other device), and provide them selectively to service providers without needing to involve a third party as intermediary. Unlike the above schemes, they offer interoperability, high privacy and security guarantees, and the ability to minimise the amount of data disclosed.
eID and the public sector
Being able to reliably identify individuals and verify their claims – that is, having a functioning eID scheme in place – is crucial for the development of e-government services and the broader digitisation of the public realm. More thoroughgoing implementation of e-government is considered to offer important benefits, including higher efficiency, easier access to public services for citizens and businesses, development of new service offerings, and (potentially, depending on architecture) greater scope for public participation and improved transparency (e.g., about what data different state agencies hold on citizens and which services they are entitled to).
However, existing eID schemes for the public sector are mostly based either on centralised or federated identity management; for instance, service-specific log-ins, smartcards (and associated card readers and software) or username/password-based systems provided by third parties – all of which come with the described drawbacks.
Moreover, hitherto many dedicated public-sector eID schemes have struggled with limited uptake among citizens. As a result, the full benefits of e-government and public sector digitisation are often yet to be realised. Reasons for slow uptake of public sector eID solutions include the prevalence, in early schemes, of complicated and sometimes expensive systems with poor usability (e.g., card reader-based solutions; need to remember multiple usernames and passwords), and lack of a sufficiently comprehensive services ecosystem, including private-sector service offerings that are accessible through the public sector’s eID. In the worst case, chicken/egg-type problems have arisen, where a dearth of service offerings led to low uptake of the solution by citizens, and low citizen uptake disincentivised businesses (and possibly state agencies) from creating the services ecosystem that could have attracted users [4, 5]. Indeed, what has happened in several countries is that rather than the private sector adopting the public sector eID scheme as the primary authentication mechanism for users, the public sector was ultimately obliged to offer its services via (usually federated/single sign on-type) schemes developed and controlled by private-sector actors (e.g. banking-sector consortia) as these enjoyed far greater uptake among the population at large (who were using them for instance for online banking) [6, 7].
SSI for public sector eID and e-government
This raises the question of the potentials of SSI for public sector eID and e-government schemes. As noted, on a general level SSI is seen to offer the advantages of greater privacy, security and user control and transparency. SSI solutions like that developed in IMPULSE can also be quite user-friendly, by virtue of providing the citizens with a single and simple process for accessing digital services via their smartphone (or other device), gone while an eID on a SIM is the winner so far.
However, it is unclear whether these advantages can suffice for SSI solutions to either strengthen uptake of e-government services, or win out against existing alternatives, such as federated solutions, where these have already developed a sizable user-base and associated services ecosystem. While the structural difference between SSI approaches and conventional centralised or federated eID schemes is, on one level, profound (full control over data and identity with the user; no third-party intermediary between the user and the service provider), on another level, these differences may also appear highly abstract to ordinary users. What societal and economic consequences they may unfold remains, so far, little understood, also because research on the real social and economic effects of SSI solutions is only beginning. By trialling an SSI solution across multiple use cases in different European countries, the IMPULSE project provides an opportunity to deepen our understanding of these issues.
[1] Kubicek, H. (2010): “Introduction: conceptual framework and research design for a comparative analysis of national eID Management Systems in selected European countries”, Identity in the Information Society 3, pp. 5–26.
[2] Strüker, J., Urbach, N., Guggenberger, T., Lautenschlager, J., Ruhland, N., Schlatt, V., Sedlmeir, J., Stoetzer, J.-C., Völter, F. (2021): “Self-Sovereign Identity – Foundations, applications, and potentials of portable digital identities.” Fraunhofer Institute for Applied Information Technology FIT, Bayreuth.
[3] Mahula, S. (2020): “Opportunities and challenges for self-sovereign identity in the public sector: a case of Belgium”, Masters Thesis submitted to the Dept. for Information Systems and Information Management, KU Leuven.
[4] Marien, I., Van Audenhove, L. (2010): “The Belgian e-ID and its complex path to implementation and innovational change”, Identity in the Information Society 3, pp. 27–41.
[5] Heichlinger, A., Gallego, P. (2010): “A new e-ID card and online authentication in Spain”, Identity in the Information Society 3, pp. 43–64.
[6] Rissanen, T. (2010): “Electronic identity in Finland: ID cards vs. bank IDs”, Identity in the Information Society 3, pp. 175–194 [7] Söderström, F. (2016): “Introducing public sector eIDs. The power of actors’ translations and institutional barriers”, PhD Thesis submitted to the Department of Management and Engineering, Linköping University.
